Update January 2026
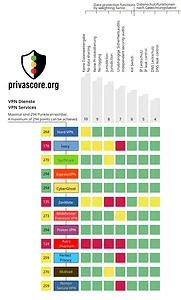
SummaryThe PRIVA SCORE evaluates VPN services regarding their privacy features and can achieve a maximum of 294 points. Proton VPN, Express VPN and CyberGhost have the highest level of data protection. Mullvad and SurfShark miss due to Jurisdiction just shy of the top rating, but due to the No-logs policy Still, solid options.
The PRIVA SCORE can receive a maximum of 294 points based on the calculation used to evaluate VPN services.
As always, the PRIVA SCORE evaluates how well apps/services Data protection features fulfill.
What is a VPN and why should you use a VPN? (Click to open and close)
- Virtual private networks (VPNs) offer a good mix of security and privacy by routing Internet traffic through a secure "tunnel". The secure tunnel leads to the provider's VPN server and encrypts all data between the end device (smartphone, computer, tablet...) and this server. This ensures that someone monitoring the traffic will not find any usable, unencrypted data.
- Data protection is increased by using such a server. Since the data traffic appears to originate from the VPN server, it is more difficult for websites to track users, collect data about them and determine their locations. A VPN service should also always be used when using a public WiFi network - for example in a café, on the train or in a shopping center. Without the VPN, the Internet provider of the public WiFi network can see the addresses of all the pages accessed, for example.
- While VPNs offer greater privacy and security, they do not provide complete anonymity. VPNs are not a perfect anonymity solution - even if some providers advertise them as such. It is true that VPNs can hide your IP address and location. This is helpful for data protection and security (see above) or when accessing blocked content. Because a VPN can bypass geographical restrictions, it is possible to access content that is blocked in your own country. This ranges from the content of streaming services to bypassing firewalls. In some autocratic states, firewalls are used to deny the population access to unadulterated information. These firewalls can be bypassed using a VPN in order to obtain unadulterated information.
- VPNs do not protect against all types of surveillance, such as browser fingerprinting (a digital fingerprint is essentially a list of characteristics that are unique to individual users, their browsers and devices used), malware or physical surveillance.
- Even if the VPN provider does not keep logs, a certain level of trust in the provider is still required. Because it is not absolutely certain how the provider will behave in the event of an official summons. Another reason: logging in with your login details on a site like Amazon results in clear identification, which a VPN obviously does not protect against.
- Complete anonymity on the Internet is virtually impossible to achieve, as there are always ways to identify users beyond a VPN. However, a VPN reduces the “attack surface”.
This update Stricter traffic light thresholds apply:
- Green (Highly recommended): 294 points – Only VPN services that all Perfectly fulfills criteria
- Yellow (Recommended with reservations): 273-259 points – VPN services with individual weaknesses in jurisdiction, audits or tracking
- Red (Not recommended): <135 points – Fundamental data protection deficiencies
This strict interpretation reflects the reality that even small data protection gaps can be problematic in today's surveillance landscape.
The Perfect Ones: Only three VPN services meet all requirements (GREEN)
ExpressVPN is one of only three VPN services to achieve the highest rating in a rigorous evaluation. Jurisdiction The British Virgin Islands are outside all surveillance alliances (5/9/14 Eyes) and do not mandate data retention. No-logs policy was through 23 independent audits Verified, including three KPMG audits (most recently in February 2025). TrustedServer technology uses exclusively RAM-based servers without hard drives. The real proof: When Turkish authorities seized the servers in 2017, no user data was found.
CyberGhost Based in Romania, the company benefits from EU data protection laws that do not require data retention. The company underwent audits in 2022 and 2024. independent audits through Deloitte Romania, who confirmed that no user activity is logged. The kill switch is permanently active and cannot be deactivated for security reasons. The transparency reports are exemplary: In Q2 2024, 534,449 legal inquiries one, which all had to be rejected because no user data existed.
ProtonVPN uses the strict Swiss data protection laws It looks ideal. Switzerland lies outside all surveillance alliances and is considered one of the most privacy-friendly countries. Jurisdictions worldwide. Successive audits by Security (2022-2024) confirmed the No-logs policy through inspection of server configurations and management systems. The transparency report documents that all official requests for information on user activity had to be rejected.
The good ones with reservations: Eight VPN services with individual weaknesses (YELLOW)
NORD VPN: Why only a YELLOW rating despite its Panama headquarters and Deloitte audits? An investigation by IT security researcher Mike Kuketz (October 2025) revealed that the NordVPN app immediately after the start Establishes data connections to Google Firebase, Firebase Crashlytics and AppsFlyer – still before User consent is not required. This violates German data protection law and GDPR principles.
On the plus side, Panama is outside the Eyes alliances, and the no-logs policy for VPN traffic has been confirmed by five audits (PwC, Deloitte). However, the app tracking disqualifies NordVPN from a green rating. stricter Interpretation of the criterion “No data sharing„.
SurfShark: Why only YELLOW? Surfshark moved from the British Virgin Islands to the Netherlands um. The Netherlands are part of the Nine Eyes AllianceThis poses theoretical surveillance risks. Strictly speaking, the fact that there is no legal obligation to retain data is not sufficient to compensate for Eyes membership.
On the positive side: A Deloitte audit in January 2023 confirmed the no-logs policy; all servers run in RAM-only mode. However, the jurisdiction prevents a green rating.
Mullvad: Why only YELLOW despite the legendary police raid? Mullvad is in Sweden resident, a 14-Eyes member. Under strict assessment, membership in a surveillance alliance carries significant weight, even though Swedish law does not oblige Mullvad to store data.
The spectacular police raid in April 2023 practically proved the no-logs policy (six officers left the office without any data), and Cure53/Assured AB conducted positive audits. But the jurisdiction prevents it from being certified green.
Bitdefender Premium VPN: Why only YELLOW? Bitdefender uses the partner's infrastructure. PangoThe audits were conducted at the infrastructure level (Aon Cyber Solutions, November 2022), not directly for Bitdefender itself. Under strict criteria, an indirect audit via a third-party provider is insufficient for a green rating.
Positive aspects: Romanian headquarters (privacy-friendly), all technical tests passed, AES-256 encryption. However, the lack of direct Big Four audits prevents a green rating.
Perfect Privacy: Why only YELLOW? Perfect Privacy has no formal audits by renowned auditing firms. Under strict assessment, the lack of independent audits is a deal-breaker for green certification, even if the server seizure in 2016 served as a "practical stress test".
Positive: Swiss jurisdiction, server seizure in 2016 yielded zero data, RAM disk operation. But without a formal audit, only a yellow rating.
Norton Secure VPN: Why only YELLOW? Norton is in the USA based in a founding member of the Five Eyes AllianceAnd given the behavior of the administration-Big Tech alliance, US jurisdiction is a fundamental problem, even if the technical implementation is flawless.
Positive: The VerSprite audit of 2025 confirmed a no-logs policy (data privacy risk: "None"), and all technical safeguards are in place. However, in the USA, the company automatically receives a yellow rating under strict assessments.
The Not Recommended: Two VPN Services with Fundamental Flaws (RED)
Ivacy: Why RED? Ivacy only inadequately meets several critical criteria:
- Singapore jurisdictionClose cooperation with Five Eyes countries
No independent auditsZero verification of the no-logs claims
Problematic parent companyGaditek also operates other VPN services with questionable data protection practices.
Under strict evaluation, the combination of unverified no-logs promises and problematic corporate structure completely disqualifies Ivacy.
Avira Phantom VPN: Why RED? Avira Phantom is the worst VPN service in the test:
Explicitly stores IP addressesNo true no-logs policy
No auditsZero independent verification
Tracking possibleIP address storage enables user tracking
Avira Phantom does not meet the minimum requirements for a privacy-oriented VPN service and is not suitable for security-conscious users. Not recommended.
Data protection features
No data sharing
The VPN provider must be technically and legally unable to share your data with third parties. This is determined by jurisdiction, infrastructure (RAM servers), and business practices.
No logging
The provider does not store any data about your online activities (websites visited, downloads, connection times). Even in the case of official inquiries, no information is available.
Jurisdiction
The legal location determines which monitoring laws the provider is subject to. 5-Eyes (USA, UK, Canada, Australia, New Zealand), 9-Eyes (+Netherlands, France, Denmark, Norway) and 14-Eyes Germany, Sweden, Belgium, Italy, and Spain have surveillance agreements. More privacy-friendly: Switzerland, Panama, the British Virgin Islands, and Romania.
Independent audits
External security experts (KPMG, Deloitte, Cure53, Securitum) verify whether the promises are kept. Audits inspect servers, code, and processes.
Kill Switch
Emergency shutdown that blocks the entire internet in case of a VPN connection failure to prevent accidental data transmission over the unprotected connection.
IP leak protection
Prevents your real IP address (which reveals your location) from being visible despite an active VPN connection.
DNS leak protection
Prevents DNS queries (website requests) from going to your internet provider's servers, where they could be logged. Good VPNs use their own encrypted DNS servers.
Conclusion: Strict assessment for maximum safety
At strict interpretation Only those who meet the data protection criteria can achieve them. ExpressVPN, CyberGhost and Proton VPN The green rating. These three VPN services perfectly meet all seven criteria without exception and are highly recommended for the highest data protection requirements.
The rated yellow Eight VPN services (NordVPN, Surfshark, Mullvad, Bitdefender, Perfect Privacy, Norton) also offer good data protection, but have individual weaknesses: problematic jurisdictions (Eyes alliances), app tracking, lack of direct audits, or US location. For most users, they are still acceptable, but not perfect.
Ivacy and Avira Phantom are under strict evaluation Not recommended: Missing audits, problematic data logging and unfavorable jurisdictions disqualify these services for privacy-conscious users.
Recommendation: Choose one of the three green-rated VPN services for maximum data protection. If budget or specific requirements are a factor, the yellow-rated services can also be considered – but be sure to check their respective limitations.
Explanation of data protection features
Independent audits: Some VPN providers have their systems and practices audited by independent third parties to ensure transparency and trust. Such audits confirm that privacy promises are being kept.
No logging: VPN providers that do not keep logs of their users do not store any information about their activities (sites visited, etc.).
No data transfer to third parties: Trustworthy VPN providers do not share their users' data with governments, authorities or other third parties. They protect the privacy of their customers.
Kill Switch: Its function is to automatically interrupt the Internet connection if the VPN connection is unexpectedly lost. The kill switch prevents the device's real IP address from being revealed if the VPN connection is lost. This ensures that users' data remains protected.
IP leak protection: This feature prevents users' real IP addresses from accidentally leaking outside the VPN tunnel and thus revealing their identity. An IP address is a unique numerical identifier assigned to each device on a computer network or the Internet to enable communication and identification between devices.
DNS leak protection: This protection ensures that DNS requests are not directed to the user's actual Internet provider, but to secure DNS servers of the VPN provider. A DNS (Domain Name System) is a distributed directory system that translates domain names into the corresponding IP addresses to enable communication between computers on the Internet.
Jurisdiction: The location of the VPN provider and the laws that apply there are important for data protection. Providers in countries with strict data protection laws offer greater security.
